
Packet Capture - Gotta Catch 'Em All
 I remember back in my junior network admin days I had to do packet capturing and analysis on devices connected to switches. I used to have to take my laptop running Wireshark, connect the NIC on the laptop to an open port on the switch I wanted to capture packets from, and then log into the switch and set up the interface as a SPAN (or mirror) so I could capture packets from a connected device and mirror the traffic to my laptop. Then I had to configure Wireshark for the specific traffic I wanted to capture. This was time consuming and if I programed the configuration for the SPAN or didn’t have Wireshark properly setup, this process could take more time than it needed to.
I remember back in my junior network admin days I had to do packet capturing and analysis on devices connected to switches. I used to have to take my laptop running Wireshark, connect the NIC on the laptop to an open port on the switch I wanted to capture packets from, and then log into the switch and set up the interface as a SPAN (or mirror) so I could capture packets from a connected device and mirror the traffic to my laptop. Then I had to configure Wireshark for the specific traffic I wanted to capture. This was time consuming and if I programed the configuration for the SPAN or didn’t have Wireshark properly setup, this process could take more time than it needed to.
Now here comes Verity from BE Networks. In the latest release, we introduce a new feature called Packet Capture. With a simple click of a button you can now collect packets through your the Verity GUI in your browser, and then take that packet capture (or PCAP) and analyze it.
In this blog post, I’m going to detail how to use this new feature with the SONiC NOS and save you (and your junior network admins) some time.
In Verity 6.4, we introduce the packet capture capability. In the Topology view, go to the switch you want to capture packets from, and zoom in to the interface that you want to capture. There is a new button on the Interface Details pane:
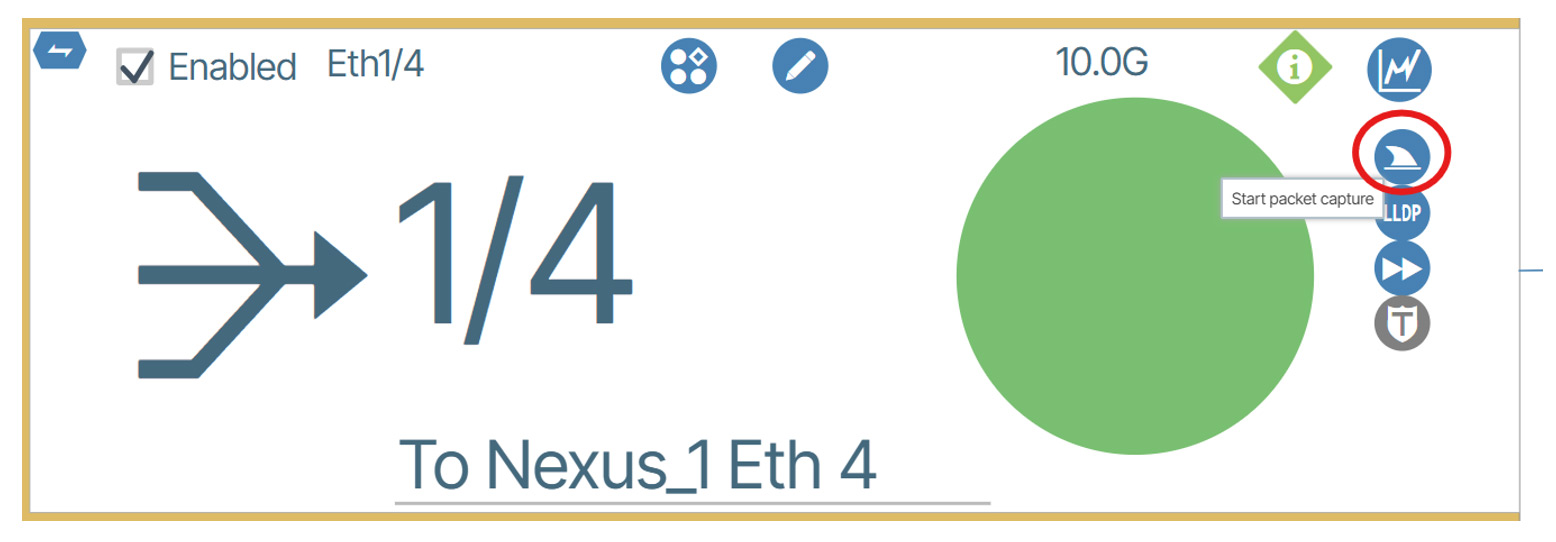
When you click this button, you are provided with the following dialog box:
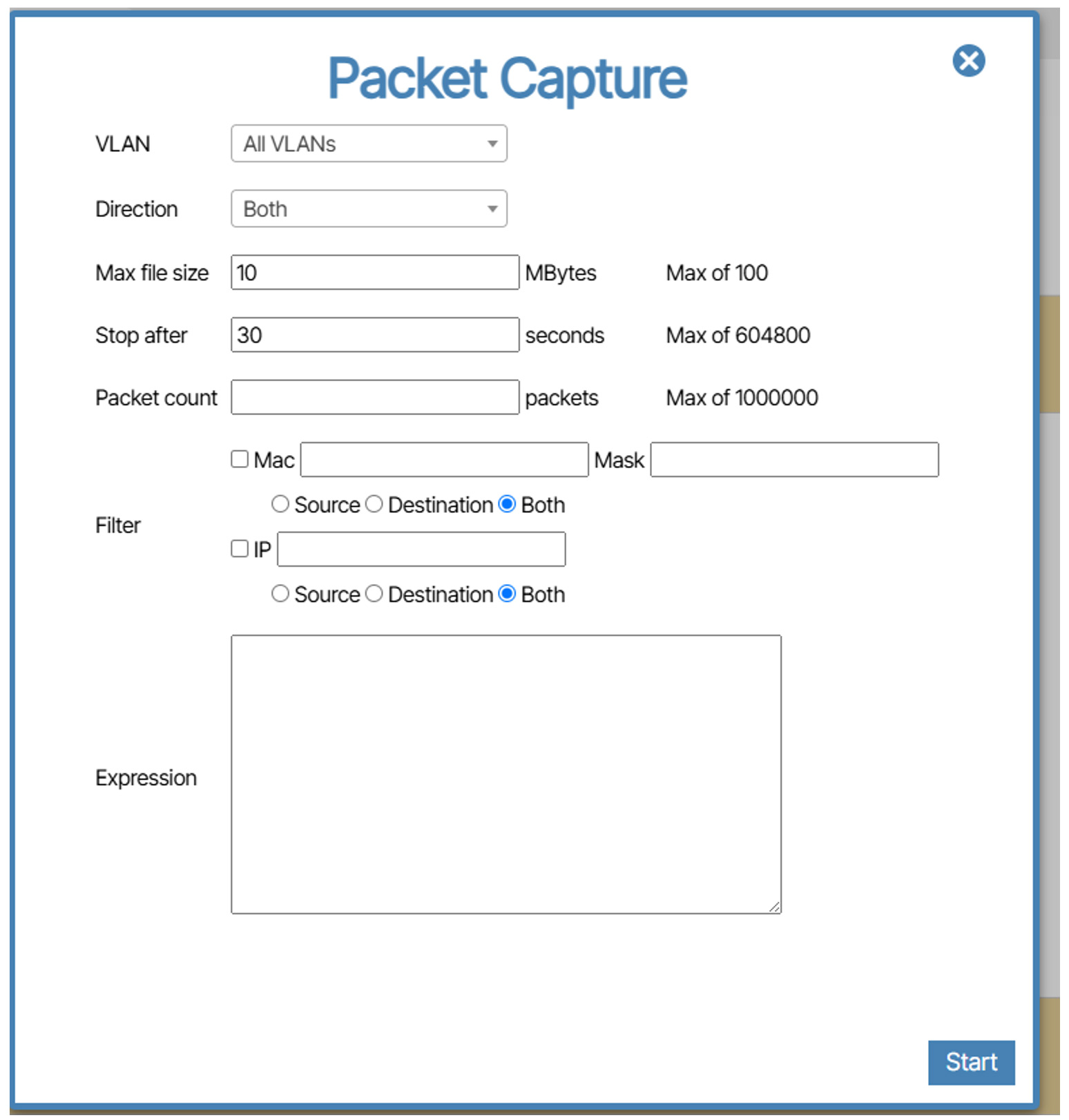
From here, you fill out the details of what to capture from the interface. You can select specific VLAN’s, what direction (TX, RX or Both), how large of a file to capture before stopping, how long (in seconds) to capture packets for, how many packets to capture before stopping, and can even specify ranges of MAC or IP addresses. There is also a Regular Expression section where you can enter specific parameters to filter traffic in the capture.
Once you click the “Start” button, the button on the Interface Details pane will change to a light green color as seen is the example below:
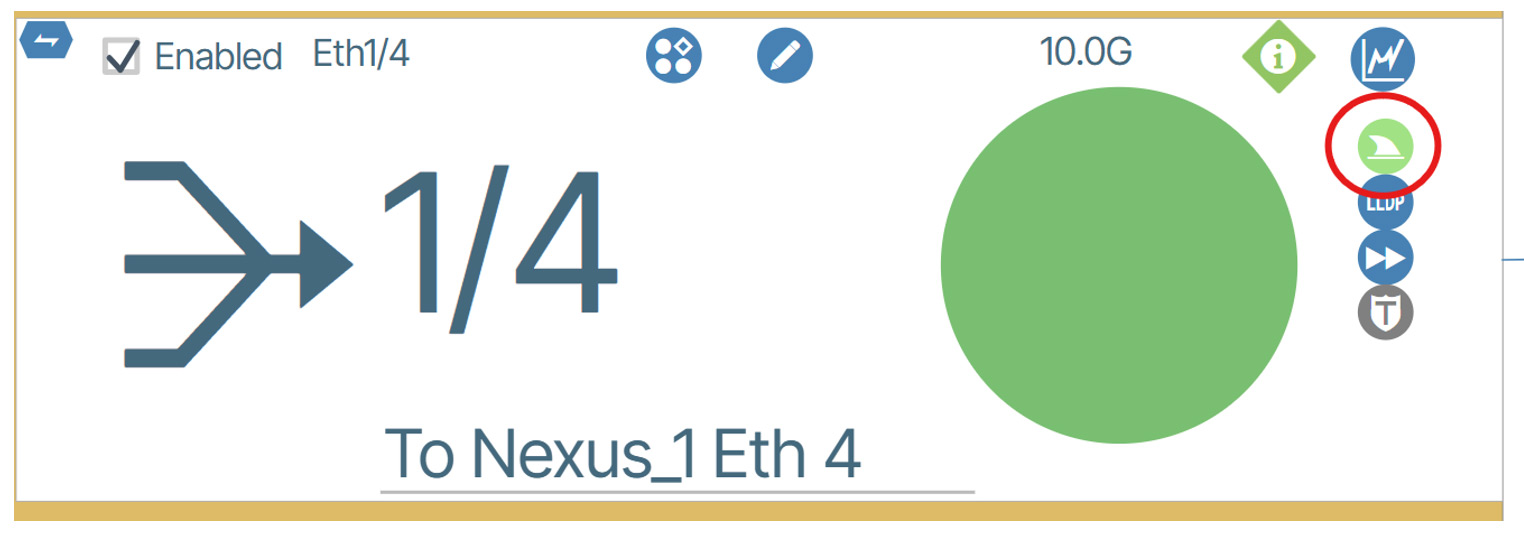
This lets you know that the capture is currently in progress. The button will change to a dark green color when it is completed the capture like in the example below:
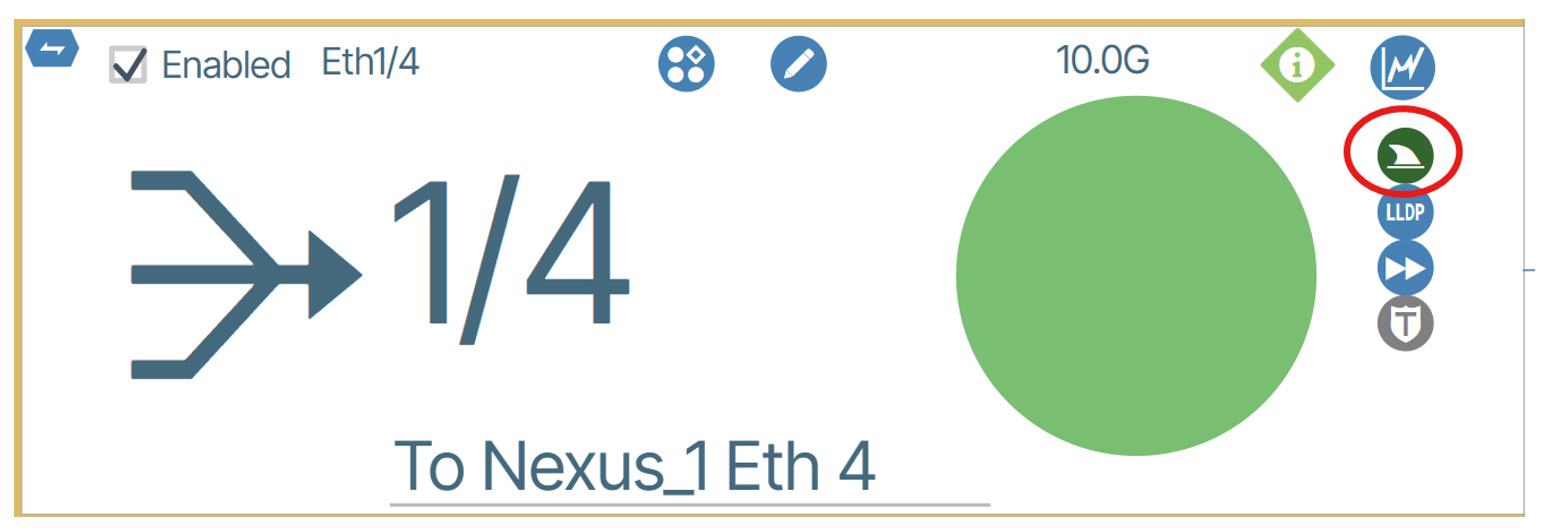
When you click the button, it will download the packet capture as a PCAP file. Once the file is downloaded, the file can be opened inside Wireshark or any other analytical tool that supports reading PCAP files. Below is an example of the packet capture contents:
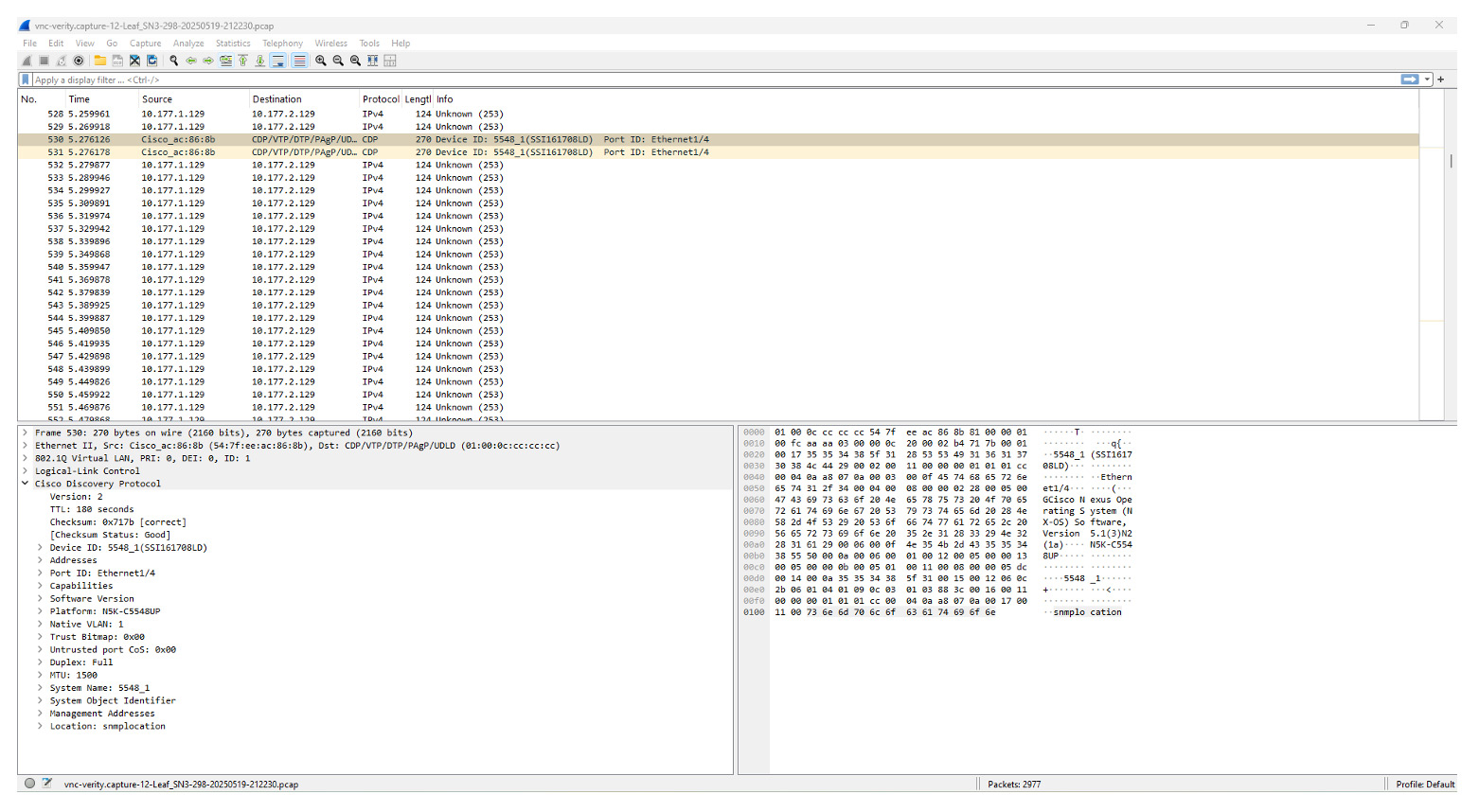
It’s as simple as that. Let’s free up some of that time doing Packet Captures using BE Networks Verity and not have to do that “Walk of Shame” and put on a Parka to go in the Data Center and collect some packets.
Do it from your desk sipping on a nice cup of coffee!

Luke Williams
Product Lead
With over 30 years experience in the IT field, there is not a whole lot Lucas hasn’t seen. From running a local ISP in his home town in Iowa when he was 16 to managing networks and server administration at the second largest newspaper media company in the United States in 2012, to developing IoT solutions and Networking NOS's while working at Canonical, he is constantly learning and trying new technologies to keep up with markets and company demands for new technologies to meet their needs. He currently is the Product Lead at BeyondEdge Networks specializing in Open Networking and SONiC.


