Network Packet Broker
Mitigate Malicious Traffic in Seconds
Build
Protocol Issues
Oversubscription
High Cost
Operate
Traffic definitions are complex
Mistakes can affect production traffic
Automate
Manually defined sources and destinationsLimited integration with analysis engines
Verity Network Packet Broker
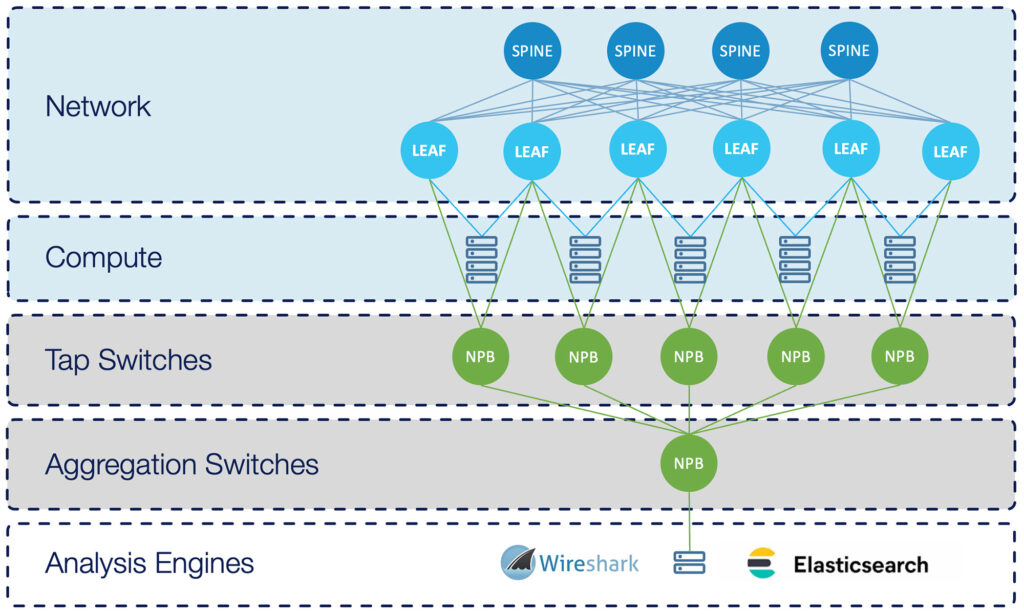
SONiC Ethernet Switches or existing tap hardware.
Fan-in multiple taps using SONiC Ethernet Switches.

Network Packet Broker Functionality
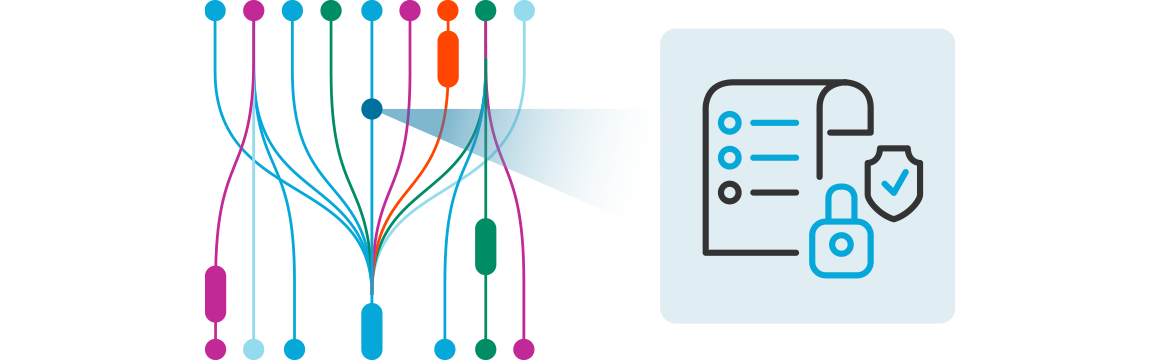
Network traffic classification allows you to prioritize or restrict specific types of data based on your defined security and performance objectives.
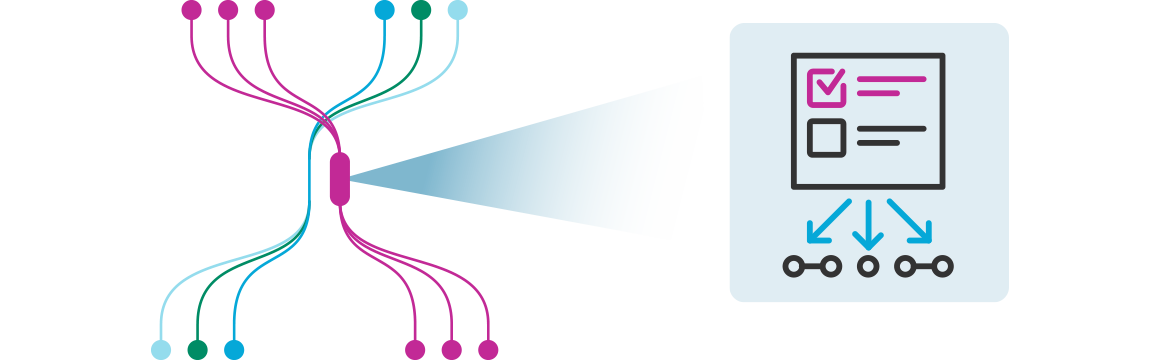
When network traffic meets specific criteria defined by filtering rules, it is identified as matching traffic and subsequently directed into the Packet Broker Network for further processing or analysis.
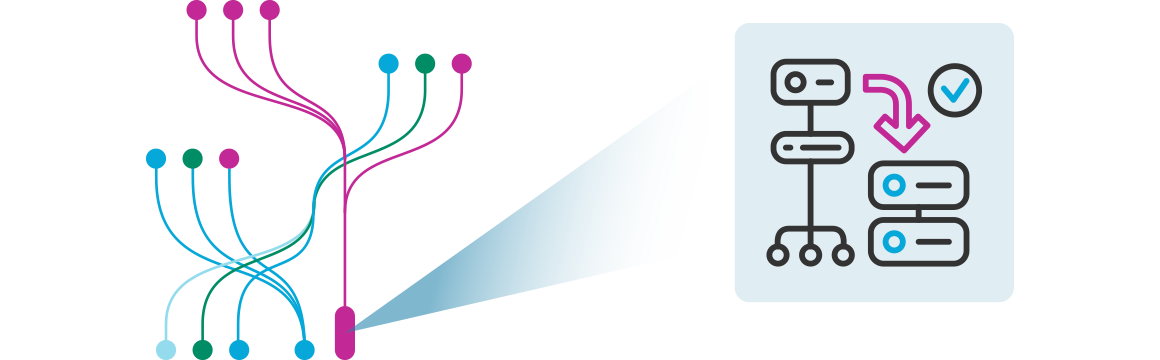
Network traffic flows are directed to the appropriate analysis tool, where they undergo detailed examination to detect potential threats or anomalies.
Simplified Deployments
Point-and-click network configuration
No taps, SPANs, or spanning tree
Simple traffic policy definitions
For more information, download the Solution Brief



